Ipsec Site To Site VPN With Strongswan and Sophos FW
First create Site To Site VPN on sophos firewal, setup whatever IPsec IKE2 policies you want, for security and performance.
Than use SSH to get in to the firewall or use Console connection.
Go to "5. Device Management" > "3. Advanced Shell"
- Use command: ls _conf/ipsec/connections/
This will show you all the config files of your existing Ipsec connection on firewall.
- Read the connection config ending .conf using command: cat _conf/ipsec/connections/
!!! Copy the configuration, you will need especially the ike..., key..., rekey..., esp, dpd... settings !!!
- You may use all, just remove "if_id_in" and "if_id_out" as Strongswan does not use this
SFVH_SO01_SFOS 20.0.0 GA-Build222# ls _conf/ipsec/connections/ connection-1.conf connection-2.conf connection.secrets SFVH_SO01_SFOS 20.0.0 GA-Build222# cat _conf/ipsec/connections/connection-1.conf # strongSwan IPsec configuration file conn connection-1 authby=psk auto=start closeaction=restart dpdaction=restart dpddelay=30 dpdtimeout=120 esp=aes256gcm16-modp2048,aes256-sha2_256-modp2048 if_id_in=1 # <<<<< this will not be used on Strongswan server if_id_out=1 # <<<<< this will not be used on Strongswan server ike=aes256-sha2_256-modp2048 ikelifetime=3600s keyexchange=ikev2 keyingtries=0 left=<Sophos WAN IP> leftid="leftsendcert=never leftsubnet=0.0.0.0/0 leftupdown=iptables lifetime=3600s reauth=no rekeyfuzz=100% rekeymargin=180s right=<IP for server where we connecting> rightid=" " rightsendcert=never rightsubnet=0.0.0.0/0 sha256_96=no type=tunnel
- Now when we got correct Ipsec Policies for first and second phase we can setup server.
- I am using Debian server, but this should work on other Linux distros too.
1. install strongswan (if something does not work try to install additional lybraries using the error codes):
- I was running this as Root, so I may not used sudo on all comands, use sudo if you do not have permissions
sudo apt-get install strongswan2. We need to create configuration file similar to one on Sophos Firewall, just paste the config rom firewall and swap left and right side
sudo nano /etc/ipsec.conf #--------------- content of /etc/ipsec.conf -------------------- config setup charondebug="ike 4, knl 4, cfg 4, net 4, esp 4, dmn 4, mgr 4" conn ussts-home # path to script what will be run on start and end of tunnel leftupdown=/usr/local/sbin/ipsec-notify.sh auto=start authby=psk # These are settings from Sophos firewall so it can connects # If VPN is not connecting check if policies are same on both sides and if you have same ID on both side too. closeaction=restart dpdaction=restart dpddelay=30 dpdtimeout=120 esp=aes256gcm16-modp2048,aes256-sha2_256-modp2048 ike=aes256-sha2_256-modp2048 ikelifetime=3600s keyexchange=ikev2 keyingtries=0 lifetime=3600s reauth=no rekeyfuzz=100% rekeymargin=180s sha256_96=no type=tunnel # Sophos firewall WAN or for any ip if you are behind NAT use %any right=%any # Mark needed for tunnel ( can be any number? ) mark_in=42 mark_out=42 # Sophos Firewall identifier, hostame needs to start with @ rightid=@fw.home.dev rightsendcert=never # here we set all networks, than we will create static routes on firewall rightsubnet=0.0.0.0/0 # Server WAN Listening interface left=66.154.25.15 # Server IP or hostname, hostame needs to start with @ to identify server side leftid="10.10.100.1" leftsendcert=never # Routes will be set up in the startup script /usr/local/sbin/ipsec-notify.sh leftsubnet=0.0.0.0/0
3. Setup Preshared Key for connection. You can use certificates if you want (RSA) but for that look up how to:
sudo nano /etc/ipsec.secrets --------------- content of /etc/ipsec.secrets -------------------- # local remote : PSK LONG_PRESHARED_KEY << this is for site to site VPN or simple connection 10.10.100.1 10.100.100.254 : PSK MY_PRESHARED_KEY # Other options, not used in this setup # If you would put here only the local IP of server or the Local identifier and : PSK, any connection with this will use same PSK 10.10.100.1 : PSK MY_PRESHARED_KEY
4. Startup and Ending script to create VTI interface for our tunnel connection:
- You will need 2 ip addresses what are not used anywhere. Best is to use /30 network as you do not need more than that.
- one IP is for server and one for the tunnel interface on Sophos firewall
nano /usr/local/sbin/ipsec-notify.sh && chmod +x /usr/local/sbin/ipsec-notify.sh ----------------- content of /usr/local/sbin/ipsec-notify.sh -------------------------- #!/bin/bash set -o nounset set -o errexit VTI_IF="vti${PLUTO_UNIQUEID}" case "${PLUTO_VERB}" in up-client) ip tunnel add "${VTI_IF}" mode vti \ local "${PLUTO_ME}" remote "${PLUTO_PEER}" \ okey "${PLUTO_MARK_OUT%%/*}" ikey "${PLUTO_MARK_IN%%/*}" ip link set "${VTI_IF}" up # Here goes virtual IP for the interface, other ip will need to be on other side f.e. Sophos tunnel ip addr add 172.28.28.1/30 dev "${VTI_IF}" # Here setup routes what are on sophos firewall and you want to have access to from Linux Server ip route add 10.100.100.0/24 dev "${VTI_IF}" sysctl -w "net.ipv4.conf.${VTI_IF}.disable_policy=1" sysctl -w "net.ipv4.conf.${VTI_IF}.rp_filter=0" sysctl -w "net.ipv4.conf.all.rp_filter=0" ;; down-client) # removes the created VTI interface ip tunnel del "${VTI_IF}" # This will delete the higher added route/routes add more if needed ip route del 10.100.100.0/24 dev "${VTI_IF}" ;; esac
5. We need to also disable strongswan automatic routes and virtual ip ( does not seem to work anyway):
nano /etc/strongswan.d/charon.conf # Find these two commands ,Uncomment them and Change it from yes to no # if you use NANO app you can press CTRL+W and typ part of the command and hit enter to find it install_routes = no install_virtual_ip = no
6. Reload configuration and restart services:
systemctl enable strongswan-starter.service --now ipsec rereadall && ipsec reload && ipsec restart # You can check the status with commands sudo systemctl status ipsec # Should be active (running) sudo ipsec status # or sudo ipsec statusall # if something is not wokring you will need to check logs: sudo tail -f /var/log/syslog # this will show last system message, good for checking if VPN has correct policies.
7. As last thing we need to setup routes on the Sophos firewall:
- I am assuming you know how to setup rules or use autogenerated rules by the VPN.
For the VPN connection you need to select these settings on Site To Site IPSec VPN:
Connection Type: Tunnel Interface
IP Version: Dual
Authentication Type: Preshared Key and use the PSK from Debian ipsec.secrets file
Listening Interface: your WAN
Gateway Address: IP of your server
Local ID: use ip or DNS - same needs to be in the server config for "rightid"
Remote ID: use ip or DNS - same needs to be in the server config for "leftid"
- if you choose DNS, you do not use @ here, it is needed only in Linux server config.
- When VPN is connected you need to go to Network and click on blue line next to your WAN interface,
select the xfrm interface and set up the second IP address from the VTI config
I have used on the Server config IP 172.28.28.1/30 so for the interface on Sophos I use 172.28.28.2/30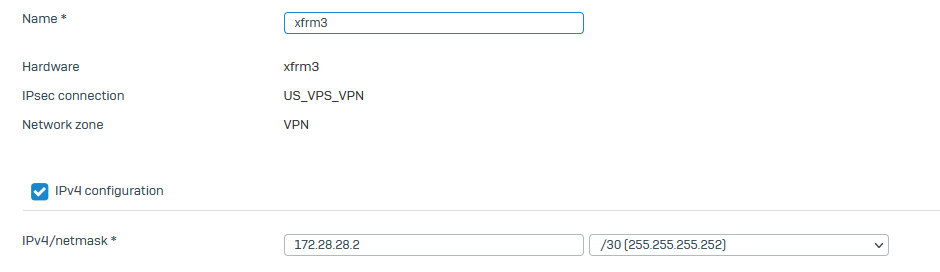
- In Routing page, Static Routes create new route and add here network what you want to access on remote server
Gateway use the VTI Ip of server interface what we setup in the VTI startup script and select Xfrm interface above: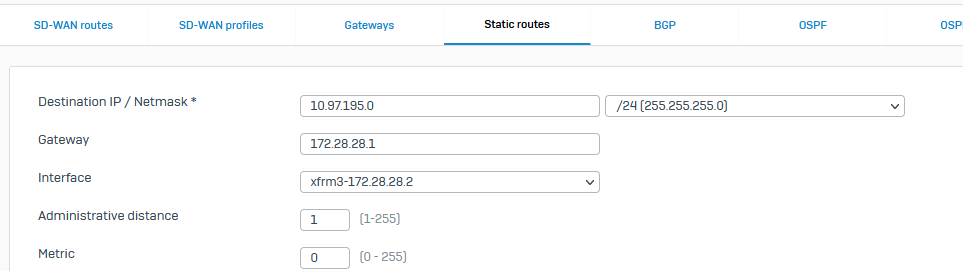
- you can also create Gateway in previous tab what can be used for SD-WAN routes if you want to route different traffic to this servers.
- good for hiding IP address for some websites.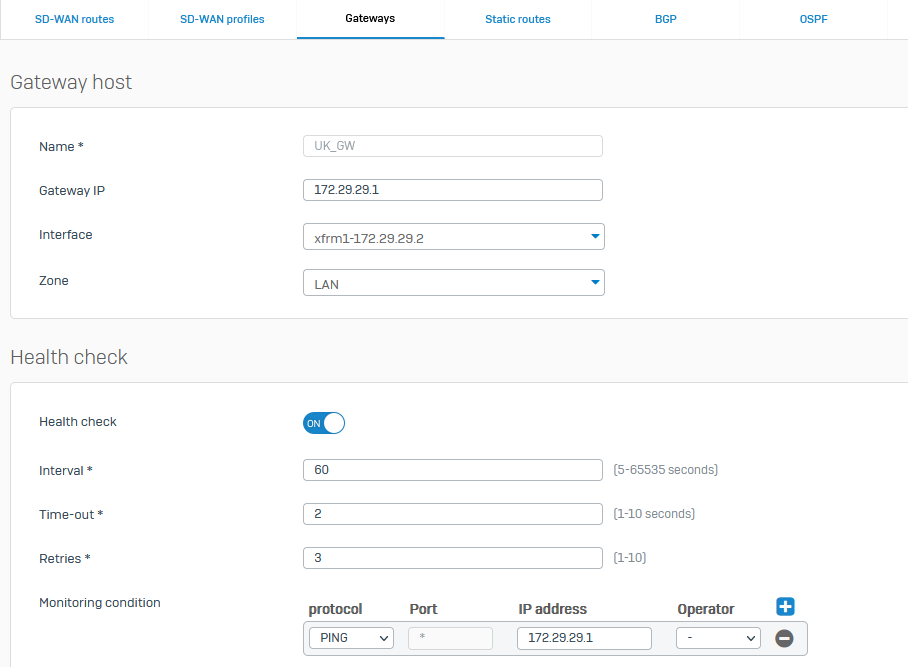
Now you should be able to ping each of the devices on server or behind Sophos FW
- if you cannot ping devices, make sure you have firewall rules on Sophos FW.
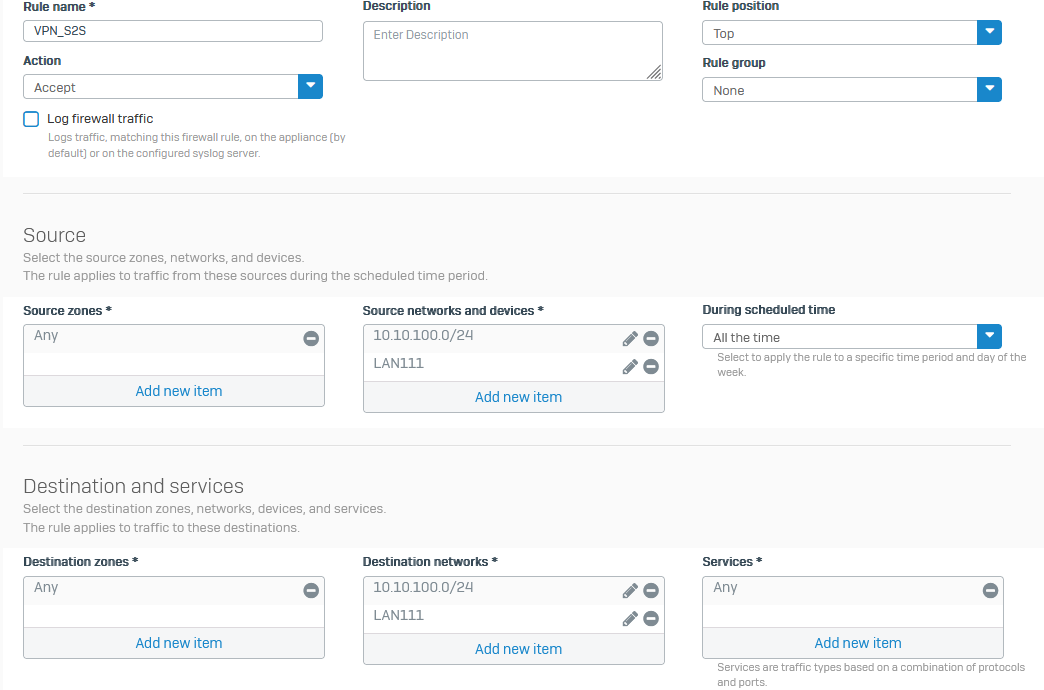
- Or you may need to add following lines on Linux server:
# adds 4 rules to /etc/sysctl.conf may need to be run as admin, or use sudo nano /etc/sysctl.conf # and add it manualy echo net.ipv4.ip_forward = 1 >> /etc/sysctl.conf echo net.ipv6.conf.all.forwarding = 1 >> /etc/sysctl.conf echo net.ipv4.conf.all.accept_redirects = 0 >> /etc/sysctl.conf echo net.ipv4.conf.all.send_redirects = 0 >> /etc/sysctl.conf # Apply new settings. sudo sysctl -p